LONDON — Google, Facebook, TikTok and other Big Tech companies operating in Europe are facing one of the most far-reaching efforts to clean up what people encounter online.
The first phase of the European Union’s groundbreaking new digital rules will take effect this week. The Digital Services Act is part of a suite of tech-focused regulations crafted by the 27-nation bloc — long a global leader in cracking down on tech giants.
The DSA, which the biggest platforms must start following Friday, is designed to keep users safe online and stop the spread of harmful content that’s either illegal or violates a platform’s terms of service, such as promotion of genocide or anorexia. It also looks to protect Europeans’ fundamental rights like privacy and free speech.
Some online platforms, which could face billions in fines if they don’t comply, have already started making changes.

Michael Dwyer
File - The Instagram logo is seen on a cell phone, Friday, Oct. 14, 2022, in Boston. Google, Facebook, TikTok and other Big Tech companies operating in Europe are facing one of the most far-reaching efforts to clean up what people encounter online. (AP Photo/Michael Dwyer, File)
Here’s a look at what’s happening this week:
WHICH PLATFORMS ARE AFFECTED?
So far, 19. They include eight social media platforms: Facebook, TikTok, Twitter, YouTube, Instagram, LinkedIn, Pinterest and Snapchat.
There are five online marketplaces: Amazon, Booking.com, China’s Alibaba AliExpress and Germany’s Zalando.
Mobile app stores Google Play and Apple’s App Store are subject, as are Google’s Search and Microsoft’s Bing search engine.
Google Maps and Wikipedia round out the list.
WHAT ABOUT OTHER ONLINE COMPANIES?
The EU’s list is based on numbers submitted by the platforms. Those with 45 million or more users — or 10% of the EU’s population — will face the DSA’s highest level of regulation.
Brussels insiders, however, have pointed to some notable omissions from the EU’s list, like eBay, Airbnb, Netflix and even PornHub. The list isn’t definitive, and it’s possible other platforms may be added later on.
Any business providing digital services to Europeans will eventually have to comply with the DSA. They will face fewer obligations than the biggest platforms, however, and have another six months before they must fall in line.
Citing uncertainty over the new rules, Facebook and Instagram parent Meta Platforms has held off launching its Twitter rival, Threads, in the EU.

Michael Dwyer
FILE - The Facebook logo is seen on a cell phone, Friday, Oct. 14, 2022, in Boston. Google, Facebook, TikTok and other Big Tech companies operating in Europe are facing one of the most far-reaching efforts to clean up what people encounter online. (AP Photo/Michael Dwyer, File)
WHAT’S CHANGING?
Platforms have started rolling out new ways for European users to flag illegal online content and dodgy products, which companies will be obligated to take down quickly and objectively.
The DSA “will have a significant impact on the experiences Europeans have when they open their phones or fire up their laptops,” Nick Clegg, Meta’s president for global affairs, said in a blog post.
Meta’s existing tools to report illegal or rule-breaking content will be easier to access, Clegg said.
Amazon opened a new channel for reporting suspected illegal products and is providing more information about third-party merchants.
TikTok gave users an “additional reporting option” for content, including advertising, that they believe is illegal. Categories such as hate speech and harassment, suicide and self-harm, misinformation or frauds and scams, will help them pinpoint the problem.
Then, a “new dedicated team of moderators and legal specialists” will determine whether flagged content either violates its policies or is unlawful and should be taken down, according to the app from Chinese parent company ByteDance.
TikTok says the reason for a takedown will be explained to the person who posted the material and the one who flagged it, and decisions can be appealed.
TikTok users can turn off systems that recommend videos and posts based on what a user has previously viewed. Facebook, Instagram and Snapchat users will have similar options. Such systems have been blamed for leading social media users to increasingly extreme posts.
The DSA prohibits targeting vulnerable categories of people, including children, with ads.
Snapchat said advertisers won’t be able to use personalization and optimization tools for teens in the EU and U.K. Snapchat users who are 18 and older also would get more transparency and control over ads they see, including “details and insight” on why they’re shown specific ads.
TikTok made similar changes, stopping users 13 to 17 from getting personalized ads “based on their activities on or off TikTok.”
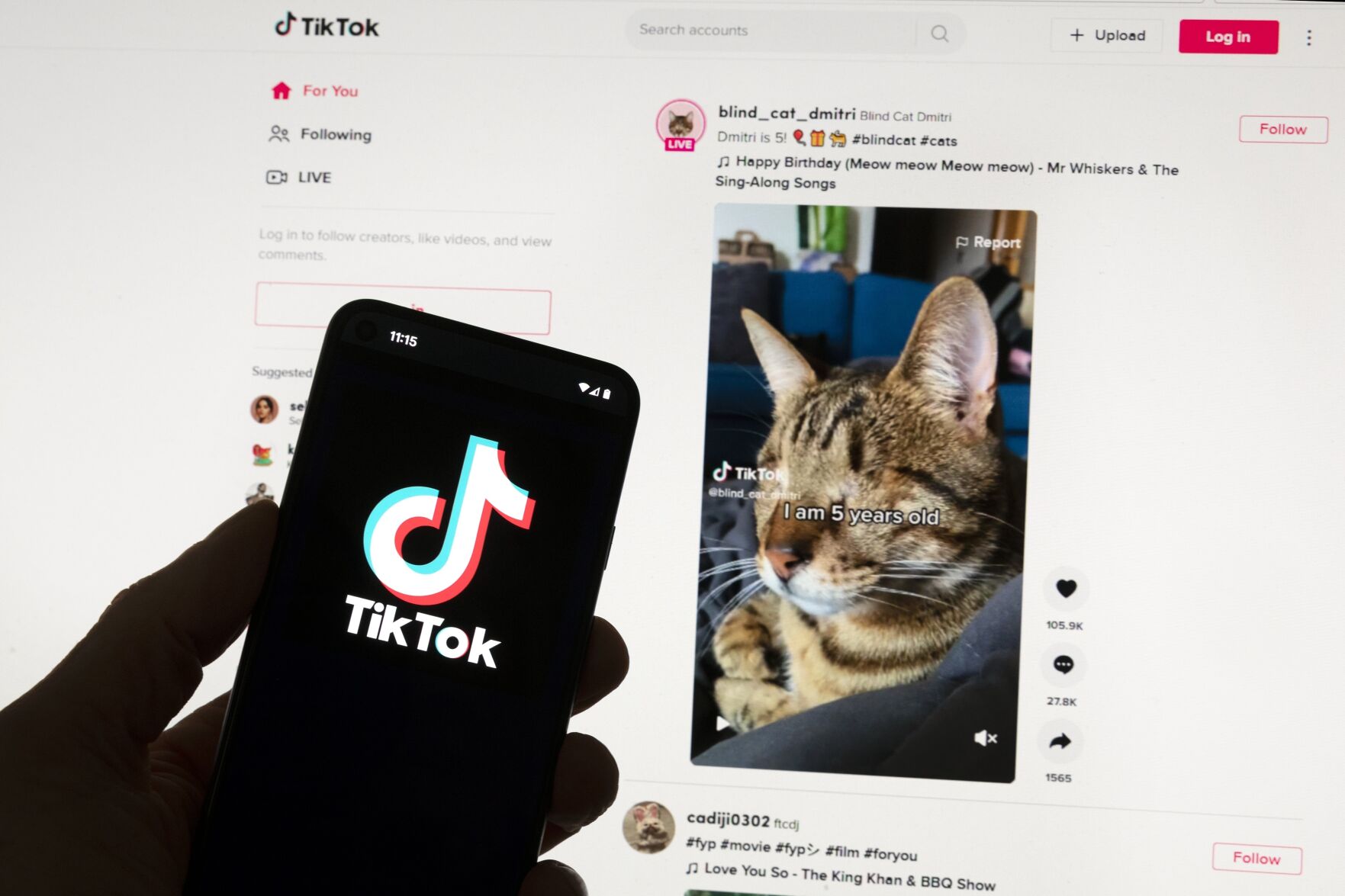
Michael Dwyer
The TikTok logo is seen on a mobile phone in front of a computer screen which displays the TikTok home screen, Saturday, March 18, 2023, in Boston. Google, Facebook, TikTok and other Big Tech companies operating in Europe are facing one of the most far-reaching efforts to clean up what people encounter online. (AP Photo/Michael Dwyer)
IS THERE PUSHBACK?
Zalando, a German online fashion retailer, has filed a legal challenge over its inclusion on the DSA’s list of the largest online platforms, arguing that it’s being treated unfairly.
Nevertheless, Zalando is launching content flagging systems for its website even though there’s little risk of illegal material showing up among its highly curated collection of clothes, bags and shoes.
The company has supported the DSA, said Aurelie Caulier, Zalando’s head of public affairs for the EU.
“It will bring loads of positive changes” for consumers, she said. But “generally, Zalando doesn’t have systemic risk (that other platforms pose). So that’s why we don’t think we fit in that category.”
Amazon has filed a similar case with a top EU court.

Matt Slocum
The Amazon app icon is seen on a smartphone, Tuesday, Feb. 28, 2023, in Marple Township, Pa. Google, Facebook, TikTok and other Big Tech companies operating in Europe are facing one of the most far-reaching efforts to clean up what people encounter online. (AP Photo/Matt Slocum)
WHAT HAPPENS IF COMPANIES DON’T FOLLOW THE RULES?
Officials have warned tech companies that violations could bring fines worth up to 6% of their global revenue — which could amount to billions — or even a ban from the EU. But don’t expect penalties to come right away for individual breaches, such as failing to take down a specific video promoting hate speech.
Instead, the DSA is more about whether tech companies have the right processes in place to reduce the harm that their algorithm-based recommendation systems can inflict on users. Essentially, they’ll have to let the European Commission, the EU’s executive arm and top digital enforcer, look under the hood to see how their algorithms work.
EU officials “are concerned with user behavior on the one hand, like bullying and spreading illegal content, but they’re also concerned about the way that platforms work and how they contribute to the negative effects,” said Sally Broughton Micova, an associate professor at the University of East Anglia.
That includes looking at how the platforms work with digital advertising systems, which could be used to profile users for harmful material like disinformation, or how their livestreaming systems function, which could be used to instantly spread terrorist content, said Broughton Micova, who’s also academic co-director at the Centre on Regulation in Europe, a Brussels-based think tank.
Big platforms have to identify and assess potential systemic risks and whether they’re doing enough to reduce them. These risk assessments are due by the end of August and then they will be independently audited.
The audits are expected to be the main tool to verify compliance — though the EU’s plan has faced criticism for lacking details that leave it unclear how the process will work.
WHAT ABOUT THE REST OF THE WORLD?
Europe’s changes could have global impact. Wikipedia is tweaking some policies and modifying its terms of use to provide more information on “problematic users and content.” Those alterations won’t be limited to Europe and “will be implemented globally,” said the nonprofit Wikimedia Foundation, which hosts the community-powered encyclopedia.
“The rules and processes that govern Wikimedia projects worldwide, including any changes in response to the DSA, are as universal as possible,” it said in a statement.
Snapchat said its new reporting and appeal process for flagging illegal content or accounts that break its rules will be rolled out first in the EU and then globally in the coming months.
It’s going to be hard for tech companies to limit DSA-related changes, said Broughton Micova, adding that digital ad networks aren’t isolated to Europe and that social media influencers can have global reach.
The regulations are “dealing with multichannel networks that operate globally. So there is going to be a ripple effect once you have kind of mitigations that get taken into place,” she said.
___
AP videojournalist Sylvain Plazy contributed from Brussels.
___
-
Europe’s sweeping rules for tech giants are about to kick in. Here’s how they work
Canva
Cybercrime is not just on the rise—it's flourishing. The increased complexity of the digital landscape and rising global technical competency have enabled hackers to innovate and adapt faster than opposing authorities can combat them.
On average, a cyberattack occurs every 39 seconds, and the effects can range from devastating to entirely unexpected. The consequences of cybercrimes are becoming more unpredictable as the landscape continues to innovate. Whereas earlier cybercrimes typically resulted in consequences like data breaches or identity theft, more recent attacks have caused power grids to shut down, equipment damage in nuclear facilities, and more.
The World Economic Forum cites the cost of cybercrime is expected to reach $10.5 trillion by 2025. For the first time, the WEC's 2023 Global Risks Report added "widespread cybercrime and cyber insecurity" to its list of the top 10 threats to global socioeconomic health over the next decade. The report pointed to "a scarcity of security experts, poor reporting habits and a lack of global agreements about how to regulate cyber threats" as the prime causes of the enormous growth in malware and ransomware attacks in recent years.
Drata compiled a list of 10 of the most impactful cybersecurity attacks from the past four decades to see how public reception of such attacks has changed over time.

Canva
Cybercrime is not just on the rise—it's flourishing. The increased complexity of the digital landscape and rising global technical competency have enabled hackers to innovate and adapt faster than opposing authorities can combat them.
On average, a cyberattack occurs every 39 seconds, and the effects can range from devastating to entirely unexpected. The consequences of cybercrimes are becoming more unpredictable as the landscape continues to innovate. Whereas earlier cybercrimes typically resulted in consequences like data breaches or identity theft, more recent attacks have caused power grids to shut down, equipment damage in nuclear facilities, and more.
The World Economic Forum cites the cost of cybercrime is expected to reach $10.5 trillion by 2025. For the first time, the WEC's 2023 Global Risks Report added "widespread cybercrime and cyber insecurity" to its list of the top 10 threats to global socioeconomic health over the next decade. The report pointed to "a scarcity of security experts, poor reporting habits and a lack of global agreements about how to regulate cyber threats" as the prime causes of the enormous growth in malware and ransomware attacks in recent years.
Drata compiled a list of 10 of the most impactful cybersecurity attacks from the past four decades to see how public reception of such attacks has changed over time.

-
Europe’s sweeping rules for tech giants are about to kick in. Here’s how they work
Canva
On Nov. 2, 1988, Robert Morris Jr., a graduate student in computer science at Cornell, launched the world's first computer worm—a malware computer program that replicates itself on other internet-connected devices, causing them to shut down. He intended the program to help him gauge the size of the internet, but a coding mistake turned the innocent experiment into a denial-of-service attack. Less than 24 hours after the eponymous worm was released, it had compromised about 1 in 10 computers connected to the internet, including systems owned by NASA and the Pentagon.
Morris became the first person to receive a felony conviction under the 1986 Computer Fraud and Abuse Act, receiving a sentence of 400 hours of community service, three years probation, and a $10,000 fine. The incident also inspired the creation of the first Computer Emergency Response Team, or CERT, at Carnegie Mellon University, which has since served as a template for cybersecurity institutions worldwide.
Canva
On Nov. 2, 1988, Robert Morris Jr., a graduate student in computer science at Cornell, launched the world's first computer worm—a malware computer program that replicates itself on other internet-connected devices, causing them to shut down. He intended the program to help him gauge the size of the internet, but a coding mistake turned the innocent experiment into a denial-of-service attack. Less than 24 hours after the eponymous worm was released, it had compromised about 1 in 10 computers connected to the internet, including systems owned by NASA and the Pentagon.
Morris became the first person to receive a felony conviction under the 1986 Computer Fraud and Abuse Act, receiving a sentence of 400 hours of community service, three years probation, and a $10,000 fine. The incident also inspired the creation of the first Computer Emergency Response Team, or CERT, at Carnegie Mellon University, which has since served as a template for cybersecurity institutions worldwide.
-
-
Europe’s sweeping rules for tech giants are about to kick in. Here’s how they work
Canva
The first cyberattack on an entire country began when Estonian authorities decided to relocate the Bronze Soldier, a Soviet Red Army memorial, to a less prominent location in the capital of Tallinn. While the statute represents victory and liberation to Russian-speaking Estonians, ethnic Estonians consider it a symbol of Soviet oppression.
On April 27, 2007, the disagreement culminated in a series of cyberattacks unleashed by Russian perpetrators on Estonian banks, government, and media outlets. Due to waves of distributed denial-of-service (DDOS) attacks, banking, government, and news services were disabled nationwide. Ultimately, the incident prompted military organizations worldwide and NATO to reevaluate the role of cybersecurity in their defense infrastructures.
Canva
The first cyberattack on an entire country began when Estonian authorities decided to relocate the Bronze Soldier, a Soviet Red Army memorial, to a less prominent location in the capital of Tallinn. While the statute represents victory and liberation to Russian-speaking Estonians, ethnic Estonians consider it a symbol of Soviet oppression.
On April 27, 2007, the disagreement culminated in a series of cyberattacks unleashed by Russian perpetrators on Estonian banks, government, and media outlets. Due to waves of distributed denial-of-service (DDOS) attacks, banking, government, and news services were disabled nationwide. Ultimately, the incident prompted military organizations worldwide and NATO to reevaluate the role of cybersecurity in their defense infrastructures.
-
Europe’s sweeping rules for tech giants are about to kick in. Here’s how they work
Canva
On Jan. 12, 2010, Google issued a statement on its blog disclosing that it had been victimized by a sophisticated cybersecurity attack—a rare public admission from a company of Google's stature. Targeted users received a link that, when clicked, instigated a chain of events using malicious JavaScript code. The code took advantage of a widely unknown vulnerability in Microsoft Internet Explorer to grant perpetrators access to system files, including intellectual property and login credentials.
The ensuing investigation revealed that the attack originated in China and targeted the Gmail accounts of human rights activists and Chinese dissidents, as well as the corporate intellectual property of dozens of companies, including Microsoft, Google, and Adobe. While officially unconfirmed, security experts worldwide attribute the attack to the Chinese government, marking the first time a government was allegedly complicit in criminal cyber activity.
Canva
On Jan. 12, 2010, Google issued a statement on its blog disclosing that it had been victimized by a sophisticated cybersecurity attack—a rare public admission from a company of Google's stature. Targeted users received a link that, when clicked, instigated a chain of events using malicious JavaScript code. The code took advantage of a widely unknown vulnerability in Microsoft Internet Explorer to grant perpetrators access to system files, including intellectual property and login credentials.
The ensuing investigation revealed that the attack originated in China and targeted the Gmail accounts of human rights activists and Chinese dissidents, as well as the corporate intellectual property of dozens of companies, including Microsoft, Google, and Adobe. While officially unconfirmed, security experts worldwide attribute the attack to the Chinese government, marking the first time a government was allegedly complicit in criminal cyber activity.
-
-
Europe’s sweeping rules for tech giants are about to kick in. Here’s how they work
Maddas // Shutterstock
Considered by some to be the world's first cyberweapon, Stuxnet was a computer worm that operated between 2007 and 2010 and targeted the Iranian nuclear program. Allegedly, U.S. and Israeli intelligence agencies joined forces in an initiative named Operation Olympic Games to sabotage the uranium centrifuges used by Iran to develop its nuclear capabilities. The worm succeeded in its mission by exploiting vulnerabilities in Microsoft Windows. Experts estimate that the operation set the Iranian nuclear program back by two years and damaged nearly 2,000 centrifuges. The incident represents one of the first examples of digital warfare and the use of computer code in international conflict.
Maddas // Shutterstock
Considered by some to be the world's first cyberweapon, Stuxnet was a computer worm that operated between 2007 and 2010 and targeted the Iranian nuclear program. Allegedly, U.S. and Israeli intelligence agencies joined forces in an initiative named Operation Olympic Games to sabotage the uranium centrifuges used by Iran to develop its nuclear capabilities. The worm succeeded in its mission by exploiting vulnerabilities in Microsoft Windows. Experts estimate that the operation set the Iranian nuclear program back by two years and damaged nearly 2,000 centrifuges. The incident represents one of the first examples of digital warfare and the use of computer code in international conflict.
-
Europe’s sweeping rules for tech giants are about to kick in. Here’s how they work
Canva
Between February 2010 and August 2015, Ukrainian hackers targeted the largest press release newswires, accessing unpublished press releases and facilitating insider trading. Vadym Iermolovych, who initiated the scheme, first accessed the newswires by purchasing stolen employee credentials.
Over the course of those five years, the hackers stole over 150,000 press releases, sold them to investors for tens of thousands of dollars, and used the information to inform their own financial moves. Authorities in the U.S. later described the incident as the world's largest known computer hacking scheme—modest estimates of the hackers' total profits start at $100 million.
Canva
Between February 2010 and August 2015, Ukrainian hackers targeted the largest press release newswires, accessing unpublished press releases and facilitating insider trading. Vadym Iermolovych, who initiated the scheme, first accessed the newswires by purchasing stolen employee credentials.
Over the course of those five years, the hackers stole over 150,000 press releases, sold them to investors for tens of thousands of dollars, and used the information to inform their own financial moves. Authorities in the U.S. later described the incident as the world's largest known computer hacking scheme—modest estimates of the hackers' total profits start at $100 million.
-
-
Europe’s sweeping rules for tech giants are about to kick in. Here’s how they work
Ken Wolter // Shutterstock
In August 2013, every customer account at Yahoo was stolen in the largest data breach ever conducted. Hackers obtained information from 3 billion accounts, including names, passwords, backup email addresses, and other data. In August 2015, investigators discovered a vendor on the darknet selling 1 billion Yahoo accounts for $300,000 and determined it was purchased by at least three buyers. However, the hackers behind the attack, as well as their motives and methods, remain largely unknown.
Some experts attribute the attack to Russian adversaries, as investigators determined that a similar attack on Yahoo the following year originated in the Russian government in an effort to spy on high-profile U.S. figures.
Ken Wolter // Shutterstock
In August 2013, every customer account at Yahoo was stolen in the largest data breach ever conducted. Hackers obtained information from 3 billion accounts, including names, passwords, backup email addresses, and other data. In August 2015, investigators discovered a vendor on the darknet selling 1 billion Yahoo accounts for $300,000 and determined it was purchased by at least three buyers. However, the hackers behind the attack, as well as their motives and methods, remain largely unknown.
Some experts attribute the attack to Russian adversaries, as investigators determined that a similar attack on Yahoo the following year originated in the Russian government in an effort to spy on high-profile U.S. figures.
-
Europe’s sweeping rules for tech giants are about to kick in. Here’s how they work
CHRISTIAN DE ARAUJO // Shutterstock
On Nov. 24, 2014, a group of hackers calling themselves the Guardians of Peace instigated a massive cyberattack against Sony Pictures. The hackers' unprecedented motive was to prevent the release of the film "The Interview," a Seth Rogen-directed comedy about an assassination attempt on the North Korean leader Kim Jong-un.
Dissatisfied with the company's response to the threat, the hackers leaked data, including embarrassing email exchanges between employees, unreleased films, employee salaries, and film concepts; deleted the company's digital infrastructure and data; and rendered nearly half of the company's computers inoperable.
The FBI described the cyberattack as one of the largest committed against the U.S., and its ensuing investigation revealed that it was sponsored by the North Korean government. This unveiled a concerning truth about the nature of cyberattacks: because they are relatively low-cost, they are easily implemented by smaller actors.
CHRISTIAN DE ARAUJO // Shutterstock
On Nov. 24, 2014, a group of hackers calling themselves the Guardians of Peace instigated a massive cyberattack against Sony Pictures. The hackers' unprecedented motive was to prevent the release of the film "The Interview," a Seth Rogen-directed comedy about an assassination attempt on the North Korean leader Kim Jong-un.
Dissatisfied with the company's response to the threat, the hackers leaked data, including embarrassing email exchanges between employees, unreleased films, employee salaries, and film concepts; deleted the company's digital infrastructure and data; and rendered nearly half of the company's computers inoperable.
The FBI described the cyberattack as one of the largest committed against the U.S., and its ensuing investigation revealed that it was sponsored by the North Korean government. This unveiled a concerning truth about the nature of cyberattacks: because they are relatively low-cost, they are easily implemented by smaller actors.
-
-
Europe’s sweeping rules for tech giants are about to kick in. Here’s how they work
Jeramey Lende // Shutterstock
On July 19, 2015, users of the infidelity-based dating site Ashley Madison logged in to find a message from hackers threatening to release users' personal information if the site was not shut down. The group of hackers, dubbed the Impact Team, claimed they intended to punish the company for profiting from harming others.
After Ashley Madison's parent company, Avid Life Media, refused the hackers' demands to shut down, the group published 120 gigabytes of user data, including names, addresses, credit card transaction information, and search histories.
Many news outlets at the time hastily publicized the names leaked during the breach, and those identified were subject to public shaming and extortion. Numerous divorces, high-profile resignations, and even suicides ensued, prompting debate over the ethics of publicizing illegally obtained personal information.
Jeramey Lende // Shutterstock
On July 19, 2015, users of the infidelity-based dating site Ashley Madison logged in to find a message from hackers threatening to release users' personal information if the site was not shut down. The group of hackers, dubbed the Impact Team, claimed they intended to punish the company for profiting from harming others.
After Ashley Madison's parent company, Avid Life Media, refused the hackers' demands to shut down, the group published 120 gigabytes of user data, including names, addresses, credit card transaction information, and search histories.
Many news outlets at the time hastily publicized the names leaked during the breach, and those identified were subject to public shaming and extortion. Numerous divorces, high-profile resignations, and even suicides ensued, prompting debate over the ethics of publicizing illegally obtained personal information.
-
Europe’s sweeping rules for tech giants are about to kick in. Here’s how they work
Brian Guest // Shutterstock
Brian Guest // Shutterstock
-
-
Europe’s sweeping rules for tech giants are about to kick in. Here’s how they work
JHVEPhoto // Shutterstock
When the credit bureau Equifax failed to install a critical security patch for its website's framework, hackers quickly took notice. On May 12, 2017, the hackers accessed Equifax's internal servers, stole employees' credentials, and extracted user information from the company's database. Over the course of 76 days, they obtained the names, Social Security numbers, birth dates, and more belongn to 147.9 million Americans, 15.2 million British citizens, and 19,000 Canadians.
The incident remains one of the largest cyberattacks involving identity theft, and the company's reputation suffered for its lax and inadequate security measures. In an eventual settlement with the Federal Trade Commission, Equifax offered impacted users a choice of free credit monitoring or a modest sum of money.
This story originally appeared on Drata and was produced and distributed in partnership with Stacker Studio.
JHVEPhoto // Shutterstock
When the credit bureau Equifax failed to install a critical security patch for its website's framework, hackers quickly took notice. On May 12, 2017, the hackers accessed Equifax's internal servers, stole employees' credentials, and extracted user information from the company's database. Over the course of 76 days, they obtained the names, Social Security numbers, birth dates, and more belongn to 147.9 million Americans, 15.2 million British citizens, and 19,000 Canadians.
The incident remains one of the largest cyberattacks involving identity theft, and the company's reputation suffered for its lax and inadequate security measures. In an eventual settlement with the Federal Trade Commission, Equifax offered impacted users a choice of free credit monitoring or a modest sum of money.
This story originally appeared on Drata and was produced and distributed in partnership with Stacker Studio.




