
Courtesy Cher Scarlett
Cher Scarlett, a software engineer, told CNN Business in an interview: "I'm looking at these pictures, and all I can think is that somebody has photoshopped my face onto porn."
Cher Scarlett, a software engineer, has a history of being misidentified by face-scanning technology, including one instance that may have surfaced a distant ancestor in a photo. So when she was introduced to an online facial-recognition tool she hadn’t heard of, she wanted to see whether it would mistake photos of her mom or daughter for her.
On February 1, Scarlett uploaded some images of her teenage daughter and her mom to PimEyes, a facial-recognition website meant to be used to find pictures of yourself from around the web — ostensibly to help stamp out issues such as revenge porn and identity theft. She didn’t get any images of herself in return — pictures of her daughter yielded other kids, she said, while one of her mom led to some pictures of her mother, plus images of other, similar-looking women.
She decided to try something else. Scarlett next uploaded a couple pictures of herself, curious if they would lead to pictures of her relatives. They didn’t, but the results stunned her anyway: tucked under some recent images of herself and mistaken matches showing photos of Britney Spears and the pop star’s sister, Jamie Lynn, were pictures of a younger version of Scarlett. They were pictures of a dark time she didn’t totally remember —a time at age 19 when, she said, she traveled to New York and was coerced into engaging in humiliating and, at times, violent sexual acts on camera.
“I’m looking at these pictures, and all I can think is that somebody has photoshopped my face onto porn,” Scarlett told CNN Business in an interview.
Scarlett, who is known for being a former Apple employee who founded the worker organizing movement known as #AppleToo, has been open online and in the media about her life and struggles, which she has said include experiencing sexual abuse as a child, dropping out of high school, battling addiction, and having nude pictures of herself shared online without her consent.
What happened to her in New York in 2005 was so traumatic that she tried to take her own life in the weeks that followed, she said, and in 2018 she began going by the last name Scarlett (she officially changed her name in December 2021).
She’s worked hard to overcome past trauma. Based in Kirkland, Washington, she’s spent years working as a software engineer. She’s raising her daughter, and she’s a recovering drug addict. Since leaving Apple in late 2021 — she has pending complaints against Apple that are being investigated by the National Labor Relations Board (Apple did not respond to a request for comment) — she began a job as a senior software engineer at video game developer ControlZee in March.
But with a few clicks of a mouse, PimEyes brought back a real-life nightmare that occurred nearly two decades ago. She has since tried and failed to get all of the explicit photos removed from PimEyes’ search results, despite the site saying it would scrub images of Scarlett from results. As of this week, sexually explicit images of Scarlett could still be found via PimEyes.
Giorgi Gobronidze, who identified himself to CNN Business as the current owner and director of PimEyes (he said he bought the company from its previous owners in December), said he wishes nobody would experience what Scarlett went through, which he acknowledged as “very, very painful.”
“However, just simply saying, ‘I don’t want to see images’ or ‘I don’t want to see the problem’ doesn’t make the problem disappear,” he said. “The problem isn’t that there is a search engine that can find these photos; the problem is there are the photos and there are people who actually uploaded and did it on purpose.”
It’s true that the discovery of unknown images may be useful for some people who are attempting to stamp out such pictures of themselves online. But Scarlett’s saga starkly shows how easily facial-recognition technology, which is now available to anyone with internet access, can lead to unexpected harms that may be impossible to undo. The technology has become increasingly common across the United States in the past several years, and there are no current federal rules regulating its use. Yet it has been blasted by privacy and digital rights groups over privacy and racial bias issues and other real and potential dangers.
More people will “undoubtedly” have experiences like Scarlett’s, said Woodrow Hartzog, a professor of law and computer science at Northeastern University. “And we know from experience that the people who will suffer first and suffer the hardest are women and people of color and other marginalized communities for whom facial-recognition technology serves as a tool of control over.”
As Scarlett put it, “I can’t imagine the horrible pain of having that part of my life exposed not by me -— by somebody else.”
“You may find this interesting”
Scarlett’s discovery of the stash of photos on PimEyes was my fault.
I’ve long been familiar with her work as a labor activist, and follow her on Twitter. Because I write often about facial-recognition software, I contacted her after she posted a confounding tweet in late January related to an experience she had on Facebook in October 2021. Scarlett had been tagged in an old-looking black-and-white picture of a woman and man — a photo that had been posted to Facebook by a friend of a friend, to whom she said she is distantly related.
She said at the time she had been “auto-tagged” via Facebook’s facial-recognition software, which was disabled after the photo had been posted; she now believes the tag was a suggestion enabled by the software. Stranger still: Some sleuthing on Ancestry.com led her to believe the woman in the photo was her great-great-great grandmother.
Laura Oliverio/CNN
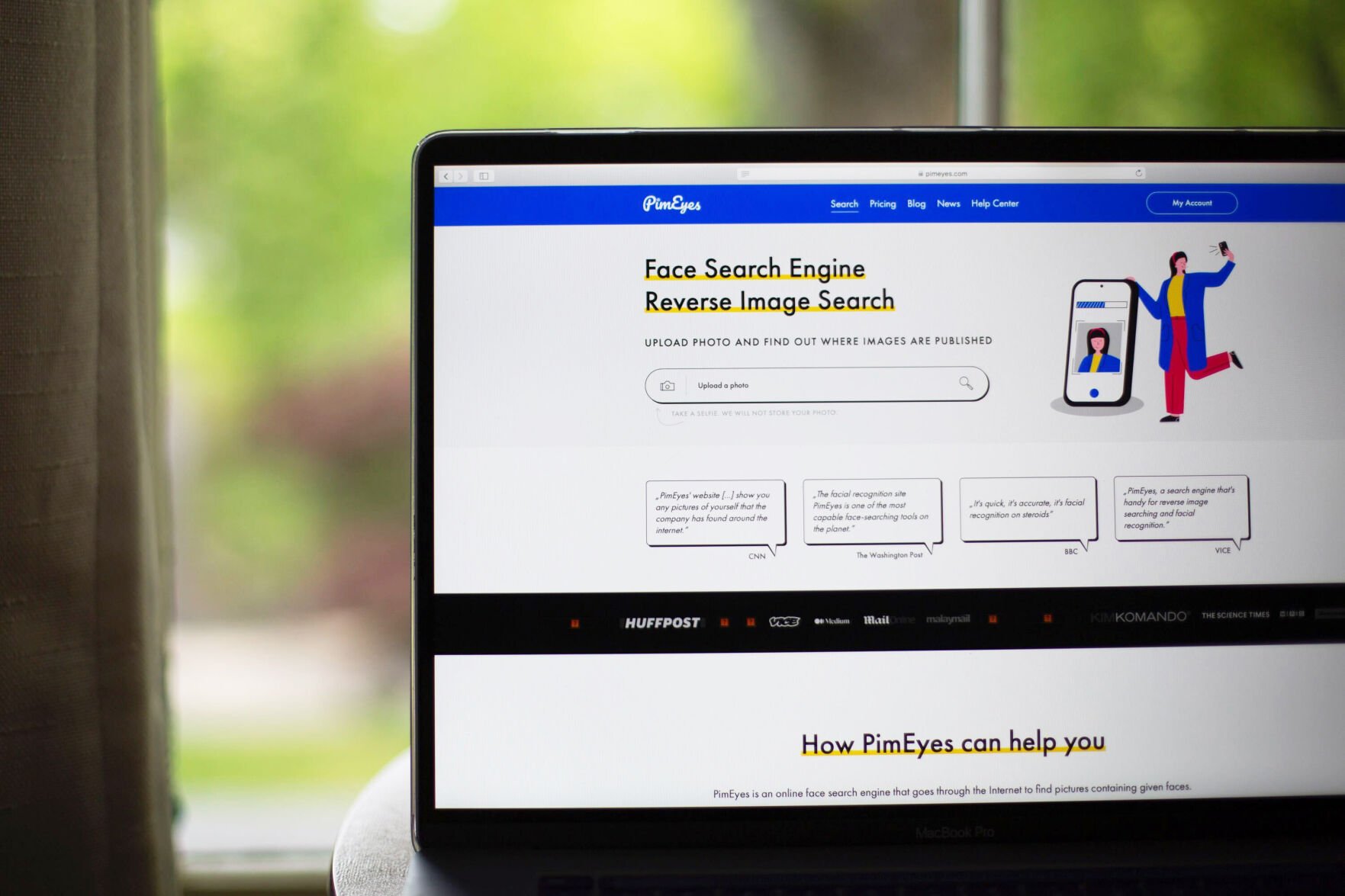
PimEyes is a facial-recognition website meant to be used to find pictures of yourself from around the web — ostensibly to help stamp out issues such as revenge porn and identity theft.
(Facebook said it never automatically tagged users in images — prior to turning off the facial-recognition feature it could, however, suggest that a user be tagged in an image if that user had the facial-recognition setting turned on, and would notify a user if they appeared in an image on Facebook but hadn’t been tagged.)
Scarlett and I talked, via Twitter’s private messages, about the strangeness of this experience and the impacts of facial-recognition software.
That’s when I sent her a link to a story I had written in May 2021 about a website called PimEyes. Though the website instructs users to search for themselves, it doesn’t stop them from uploading photos of anyone. And while it doesn’t explicitly identify anyone by name, as CNN Business discovered by using the site, that information may be just clicks away from the images PimEyes pulls up.
Its images come from a range of websites, including company, media and pornography sites — the last of which PimEyes told CNN Business in 2021 that it includes so people can search online for any revenge porn in which they may unknowingly appear. PimEyes says it doesn’t scrape images from social media.
“You may find this interesting,” I wrote, introducing my article.
Minutes later, Scarlett told me she had paid $30 for PimEyes’ cheapest monthly service. (PimEyes shows users a free, somewhat blurred preview of each image that its facial-recognition software determines is likely to include the same person as in the photo that the user initially uploaded; you have to pay a fee to click through to go to the websites where the images appear.)
Shortly after that, she sent me a message: “oh no.”
Processing the results
It took Scarlett time to process what she was seeing in the results, which included images related to the forced sex acts that were posted on numerous websites.
At first, she thought it was her face pasted on someone else’s body; then, she wondered, why did she look so young? She saw one image of her face, in which she recalls she was sitting down; she recognized the shirt she was wearing in the photo, and the hair.
She sent me this photo, which appears benign without Scarlett’s context — it shows a younger version of herself, with dark brown hair parted in the center, a silvery necklace around her neck, wearing a turquoise tank top.
She saved a copy of this image and used it to conduct another search, which she said yielded dozens more explicit images, many aggregated on various websites. Some images were posted to websites devoted to torture porn, with words like “abuse,” “choke,” and “torture” in the URLs.
“And it was just like,” Scarlett said, pausing and making a kind of exploding-brain sound as she described what it was like to stare at the images. In an instant, she realized how memories she had of her brief time in New York didn’t all match up with what was in the photos.
“It’s like there’s this part of my brain that’s hiding something, and part of my brain that’s looking at something, and this other part of my brain that knows this thing to be true, and they all just collided into each other,” she said. “Like, this thing is no longer hidden from you.”
Adam Massey, a partner at CA Goldberg Law who specializes in issues such as non-consensual pornography and technology-facilitated abuse, said for many people he’s worked with it can feel like “a whole new violation” every time a victim encounters these sorts of images.
“It’s incredibly painful for people and every time it’s somewhere new it is a new jolt,” he said.
Not only did Scarlett see more clearly what had happened to her, she also knew that anyone who looked her up via PimEyes could find them. Whereas in past decades such imagery might be on DVDs or photos or VHS tapes, “it’s forever on the internet and now anybody can use facial-recognition software and find it,” she said.
Opting out
Scarlett quickly upgraded her PimEyes subscription to the $80-per-month service, which helps people “manage” their search results, such as by omitting their image results from PimEyes’ public searches.
Scarlett got help in sending out DMCA takedown requests to websites hosting images she wanted taken down, she said. She isn’t the copyright owner of the images, however, and the requests were ignored.
Scarlett is angry that people don’t have the right to opt in to PimEyes. The website doesn’t require users to prove who they are before they can search for themselves, which might prevent some forms of use or abuse of the service (say, an employer looking up prospective employees or a stalker looking up victims).
Gobronidze said PimEyes operates this way because it doesn’t want to amass a large database of user information, such as photographs and personal details. It currently stores facial geometry associated with photos, but not photos, he said.
“We do not want to turn into a monster that has this huge number of people’s photography,” he said.
Users can opt out of PimEyes’ search results for free, but Scarlett’s story shows this detail can be easy to miss. Users first have to find the link (it’s in tiny gray text atop a black background on the bottom right of PimEyes’ website); it requires filling out a form, uploading a clear image of the person’s face, and verifying their identity with an image of an ID or passport.
“It’s definitely not very accessible,” said Lucie Audibert, legal officer with London-based human rights group Privacy International.
Gobronidze said the option to opt out will become easier to find with a website update that’s in the works. He also shared a link that anyone can use to request PimEyes take data pertaining to specific photos of their face out of its index, which he said will become easier to find in the future as well. He also wants users to know they don’t need to pay to opt out, and said the company plans to publish a blog post about the opt-out process this week.
Scarlett did opt out, saying she asked PimEyes to remove her images from its search results in mid-March.
She hadn’t heard anything from PimEyes as of April 2, when she chronicled what she went through on Medium — a decision she made in part because she was hoping PimEyes would respond by honoring her request.
It was about more than that, though, she said.
“We need to look at facial recognition software and how it’s being used, in terms of [how] we’re losing our anonymity but also the far-reaching consequences of losing that anonymity and letting anybody put in a picture of our face and find everywhere we’ve been on the internet or in videos,” she said.
Also in early April, Scarlett upgraded to PimEyes’ $300 “advanced” tier of service, which includes the ability to conduct a deeper web search for images of your face. That yielded yet more explicit pictures of herself.
On April 5 — three days after publishing her Medium post and tweeting about her experience — PimEyes approved Scarlett’s request to opt out of its service, according to an email from PimEyes that Scarlett shared with CNN Business.
“Your potential results containing your face are removed from our system,” the email said.
Gobronidze told CNN Business that PimEyes generally takes no more than 24 hours to approve a user’s opt-out request.
“The images will resurface”
But as of May 19, plenty of images of Scarlett — including sexually explicit ones — were still searchable via PimEyes. I know because I paid $30 for one month’s access to PimEyes and searched for images of Scarlett with her permission.
First, I tried using the recent picture of Scarlett that appears in this article — a photo she took in May. PimEyes reported 73 results, but only showed me two of them: one of Scarlett with bleached hair, which led to a dead link, and another of her smiling slightly, which led to a podcast episode in which she was interviewed.
Below the results, PimEyes’s website encouraged me to pay more: “If you would like to see what results can be found using a more thorough search called Deep Search, purchase the Advanced plan,” it read, with the last four words underlined and linked to PimEyes’ pricing plans.
Next, I tried an image of Scarlett from 2005 that she instructed me to use: the one of her in a sleeveless turquoise top with a necklace on, which she said was the same image she sent to PimEyes to opt her out of its search results. The results were far more disturbing.
Alongside a handful of recent photos of Scarlett from news articles were numerous sexually explicit images that appeared to be from the same time period as the image I used to conduct the search.
This shows the opt-out process “sets people up to fight a losing battle,” Hartzog, the law professor, said, “because this is essentially like playing whack-a-mole or Sisyphus forever rolling the boulder up the hill.”
“It will never stop,” he said. “The images will resurface.”
Gobronidze acknowledged that PimEyes’ opt-out process doesn’t work how people expect. “They simply imagine that they will upload a photo and this photo will disappear from the search results,” he said.
The reality is more complicated: Even after PimEyes approves an opt-out request and blocks the URLs of similar-seeming photos, it can’t always stamp out all images of a person that have been indexed by the company. And it’s always possible that the same or similar photos of a person will pop up again as the company continuously crawls the internet.
Gobronidze said users can include multiple pictures of themselves in an opt-out request.
Scarlett still has questions, such as what PimEyes plans to do to prevent what happened to her from happening to anyone else. Gobronidze said part of this will come via making it clearer to people how to use PimEyes, and through improving its facial-recognition software so that it can better eliminate images that users don’t want to show up in the site’s search results.
“We want to ensure that these results are removed for once and all,” he said.
Scarlett, meanwhile, remains concerned about the potential for facial-recognition technology in the future.
“We need to take a hard stop and look at technology — especially this kind of technology — and say, ‘What are we doing? Are we regulating this enough?'” she said.
***
-
She thought a dark moment in her past was forgotten. Then she scanned her face online.
Bettmann // Getty Images
Privacy is both a moving target and a living thing, requiring constant updates to the American body of law in order to keep up.
From the end of the American Revolution to the present, Zapproved compiled a timeline of federal privacy law in the United States. These landmark pieces of writing or legislation illustrate the extent to which privacy—and how it’s defined and regulated—has played a role in the American way of life since the time of the country’s Founding Fathers.
Following the writing of the U.S. Constitution in 1787 (ratified in 1788 and operational since 1789), colonists ratified the Bill of Rights in December of 1791. These constitutional amendments represented essential liberties that colonists claimed at the time, including the First Amendment protecting freedom of speech and the Second Amendment affirming all citizens’ rights to keep and bear arms.
The little-publicized Third Amendment, which prohibited the federal government from requiring households, private businesses, or local governments to house soldiers, may seem abstract today. But that amendment ultimately established a level of protection for an American citizen’s right to ownership and use of property without government interference.
Keep reading to learn more about how American culture, invention, and adoption of technology helped to shape how we perceive and legislate privacy in our own homes, in public, and online.

Bettmann // Getty Images
Privacy is both a moving target and a living thing, requiring constant updates to the American body of law in order to keep up.
From the end of the American Revolution to the present, Zapproved compiled a timeline of federal privacy law in the United States. These landmark pieces of writing or legislation illustrate the extent to which privacy—and how it’s defined and regulated—has played a role in the American way of life since the time of the country’s Founding Fathers.
Following the writing of the U.S. Constitution in 1787 (ratified in 1788 and operational since 1789), colonists ratified the Bill of Rights in December of 1791. These constitutional amendments represented essential liberties that colonists claimed at the time, including the First Amendment protecting freedom of speech and the Second Amendment affirming all citizens’ rights to keep and bear arms.
The little-publicized Third Amendment, which prohibited the federal government from requiring households, private businesses, or local governments to house soldiers, may seem abstract today. But that amendment ultimately established a level of protection for an American citizen’s right to ownership and use of property without government interference.
Keep reading to learn more about how American culture, invention, and adoption of technology helped to shape how we perceive and legislate privacy in our own homes, in public, and online.

-
She thought a dark moment in her past was forgotten. Then she scanned her face online.
Alexi Rosenfeld // Getty Images
The fourth entry in the Bill of Rights offers citizens protection from “unreasonable searches and seizures... and no Warrants shall issue, but upon probable cause, supported by Oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.”
This is often shortened to “no unreasonable search,” safeguarding the public from government searches of property or person without due cause. In most cases, that cause requires a warrant, except in the case of emergencies or when “probable cause” is up to the judgment of police.
Alexi Rosenfeld // Getty Images
The fourth entry in the Bill of Rights offers citizens protection from “unreasonable searches and seizures... and no Warrants shall issue, but upon probable cause, supported by Oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.”
This is often shortened to “no unreasonable search,” safeguarding the public from government searches of property or person without due cause. In most cases, that cause requires a warrant, except in the case of emergencies or when “probable cause” is up to the judgment of police.
-
-
She thought a dark moment in her past was forgotten. Then she scanned her face online.
Vintage Images // Getty Images
When Kodak introduced the first popular amateur camera, the company opened a floodgate of concerns about privacy as it became viable for virtually anyone to spy on or document the actions of their family, friends, and neighbors—not to mention celebrities and politicians. By the time Kodak’s founder, George Eastman, released the mass-produced Kodak Brownie camera in 1900 for $1 a pop, photography had officially gone mainstream.
While photography is protected by the First Amendment, there are many documented cases even today of photographers being compelled to defend their use of photography in public spaces. And although public photographs of people are also protected, by 1890 a person’s right to their own likeness was called into question.
Vintage Images // Getty Images
When Kodak introduced the first popular amateur camera, the company opened a floodgate of concerns about privacy as it became viable for virtually anyone to spy on or document the actions of their family, friends, and neighbors—not to mention celebrities and politicians. By the time Kodak’s founder, George Eastman, released the mass-produced Kodak Brownie camera in 1900 for $1 a pop, photography had officially gone mainstream.
While photography is protected by the First Amendment, there are many documented cases even today of photographers being compelled to defend their use of photography in public spaces. And although public photographs of people are also protected, by 1890 a person’s right to their own likeness was called into question.
-
She thought a dark moment in her past was forgotten. Then she scanned her face online.
Library of Congress/Corbis/VCG // Getty Images
Warren and Brandeis’ influential 1890 article “The Right to Privacy,” published in the Harvard Law Review, picks up many of the thorny issues raised by the first availability of Kodak’s amateur camera.
“The Right to Privacy” was widely considered among the most influential law review articles written and has been credited with pushing more than a dozen state courts to recognize similar laws to individuals’ rights to privacy. Among those bills was New York’s adoption of sections 50 and 51 in its Civil Rights Law, affirming individuals’ rights to the use of their own likeness.
Suggestions outlined by Warren and Brandeis further paved the way for other state laws, such as rendering the recording of private conversations without both parties’ consent illegal. Other issues, like whether people running for public office should still have privacy in their personal dealings and actions, continue being debated today.
Library of Congress/Corbis/VCG // Getty Images
Warren and Brandeis’ influential 1890 article “The Right to Privacy,” published in the Harvard Law Review, picks up many of the thorny issues raised by the first availability of Kodak’s amateur camera.
“The Right to Privacy” was widely considered among the most influential law review articles written and has been credited with pushing more than a dozen state courts to recognize similar laws to individuals’ rights to privacy. Among those bills was New York’s adoption of sections 50 and 51 in its Civil Rights Law, affirming individuals’ rights to the use of their own likeness.
Suggestions outlined by Warren and Brandeis further paved the way for other state laws, such as rendering the recording of private conversations without both parties’ consent illegal. Other issues, like whether people running for public office should still have privacy in their personal dealings and actions, continue being debated today.
-
-
She thought a dark moment in her past was forgotten. Then she scanned her face online.
GHI/Universal History Archive via Getty Images
It’s resoundingly commonplace for the U.S. federal government to limit civilian rights during wartime, from President Lincoln’s suspension of habeas corpus during the Civil War or the internment of Japanese Americans during World War II.
The Espionage Act of 1917 pulls a page from the same playbook. In it, the government outlines that certain dangerous ideas are “enemies” of the United States and can be punished by law. These ideas included certain actions, like whistleblowing, considered harmful at the time to the United States armed forces.
Edward Snowden is one of the most high-profile people to have been charged with crimes against the state under this act.
GHI/Universal History Archive via Getty Images
It’s resoundingly commonplace for the U.S. federal government to limit civilian rights during wartime, from President Lincoln’s suspension of habeas corpus during the Civil War or the internment of Japanese Americans during World War II.
The Espionage Act of 1917 pulls a page from the same playbook. In it, the government outlines that certain dangerous ideas are “enemies” of the United States and can be punished by law. These ideas included certain actions, like whistleblowing, considered harmful at the time to the United States armed forces.
Edward Snowden is one of the most high-profile people to have been charged with crimes against the state under this act.
-
She thought a dark moment in her past was forgotten. Then she scanned her face online.
DJSinop // Shutterstock
In 1890, Warren and Brandeis examined the existing body of law in order to discuss privacy as a legal ideal. By 1960, William Prosser, the dean of the University of California–Berkeley’s law school, nailed down his choice of four torts concerning privacy.
A tort is a cause allowing people to sue in civil court for financial damages. Prosser’s torts concern intrusion into private life, disclosure of embarrassing facts, misleading publicity, and appropriation of someone’s likeness. In the modern age, critics of Prosser’s privacy torts say the list, while influential, does not adequately protect people from intrusions such as data gathering or identity theft.
DJSinop // Shutterstock
In 1890, Warren and Brandeis examined the existing body of law in order to discuss privacy as a legal ideal. By 1960, William Prosser, the dean of the University of California–Berkeley’s law school, nailed down his choice of four torts concerning privacy.
A tort is a cause allowing people to sue in civil court for financial damages. Prosser’s torts concern intrusion into private life, disclosure of embarrassing facts, misleading publicity, and appropriation of someone’s likeness. In the modern age, critics of Prosser’s privacy torts say the list, while influential, does not adequately protect people from intrusions such as data gathering or identity theft.
-
-
She thought a dark moment in her past was forgotten. Then she scanned her face online.
Bettmann // Getty Images
Until 1965, Comstock Laws—which aimed to prevent the sale of licentious materials like pornography—also ensured the illegality of selling contraceptives.
Estelle Griswold, the head of Connecticut’s branch of Planned Parenthood at the time, went before the Supreme Court to represent the movement to legalize contraceptives. The Court ruled to legalize the sale of contraceptives, finding the Constitution protects a married couple’s right to marital privacy and protection from state restrictions on contraception.
Bettmann // Getty Images
Until 1965, Comstock Laws—which aimed to prevent the sale of licentious materials like pornography—also ensured the illegality of selling contraceptives.
Estelle Griswold, the head of Connecticut’s branch of Planned Parenthood at the time, went before the Supreme Court to represent the movement to legalize contraceptives. The Court ruled to legalize the sale of contraceptives, finding the Constitution protects a married couple’s right to marital privacy and protection from state restrictions on contraception.
-
She thought a dark moment in her past was forgotten. Then she scanned her face online.
Bettmann // Getty Images
Charles Katz was a wildly successful bookie in Los Angeles who calculated the fluctuating odds that one team would win over the other—known as “handicapping.” The FBI, suspicious Katz was illegally communicating gambling information to clients in other states, discovered he was using a payphone to relay information to clients.
Because the payphone was technically public, the FBI was able to use eavesdropping technology to catch Katz red-handed and convict him on eight counts for illegally transmitting wagering information to Boston and Miami.
Katz and his attorneys appealed the decision all the way up, with the Supreme Court ultimately ruling that people have the right to Fourth Amendment protections and a reasonable expectation of privacy, even in public places. This ruling has been particularly influential in the internet age.
Bettmann // Getty Images
Charles Katz was a wildly successful bookie in Los Angeles who calculated the fluctuating odds that one team would win over the other—known as “handicapping.” The FBI, suspicious Katz was illegally communicating gambling information to clients in other states, discovered he was using a payphone to relay information to clients.
Because the payphone was technically public, the FBI was able to use eavesdropping technology to catch Katz red-handed and convict him on eight counts for illegally transmitting wagering information to Boston and Miami.
Katz and his attorneys appealed the decision all the way up, with the Supreme Court ultimately ruling that people have the right to Fourth Amendment protections and a reasonable expectation of privacy, even in public places. This ruling has been particularly influential in the internet age.
-
-
She thought a dark moment in her past was forgotten. Then she scanned her face online.
Nirat.pix // Shutterstock
The Privacy Act of 1974 deals with the way federal agencies handle the data of Americans. It came about in response to public concerns about how the creation and use of computerized databases, first introduced in the ’60s, could affect individual privacy rights.
The act establishes that agencies must secure records, keeping them safe unless the person in the record explicitly signs off on any additional use. People also have the right to see and amend what their federal agency records may say about them.
There are a number of exemptions given to the Privacy Act of 1974, including for simple statistical purposes like the U.S. Census as well as more salient law enforcement reasons. There are also de facto exemptions because of the number of records that are held outside of strictly “agencies,” like those of U.S. courts.
Nirat.pix // Shutterstock
The Privacy Act of 1974 deals with the way federal agencies handle the data of Americans. It came about in response to public concerns about how the creation and use of computerized databases, first introduced in the ’60s, could affect individual privacy rights.
The act establishes that agencies must secure records, keeping them safe unless the person in the record explicitly signs off on any additional use. People also have the right to see and amend what their federal agency records may say about them.
There are a number of exemptions given to the Privacy Act of 1974, including for simple statistical purposes like the U.S. Census as well as more salient law enforcement reasons. There are also de facto exemptions because of the number of records that are held outside of strictly “agencies,” like those of U.S. courts.
-
She thought a dark moment in her past was forgotten. Then she scanned her face online.
Spencer Grant // Getty Images
By the 1980s, technology had again begun to accelerate leagues ahead of the existing body of privacy law. Consumers began to use home computers with rudimentary modem technology. People at public universities and government facilities were connected in the earliest form of what later became the internet. These emerging networks warranted a new kind of privacy protection.
The Cable Communications Policy Act of 1984, The Electronic Communications Privacy Act of 1986, and the Video Privacy Protection Act of 1988, among others like them, sought to protect people from the computer equivalent of wiretaps, making it illegal to “listen in” on regular electronic communications.
Spencer Grant // Getty Images
By the 1980s, technology had again begun to accelerate leagues ahead of the existing body of privacy law. Consumers began to use home computers with rudimentary modem technology. People at public universities and government facilities were connected in the earliest form of what later became the internet. These emerging networks warranted a new kind of privacy protection.
The Cable Communications Policy Act of 1984, The Electronic Communications Privacy Act of 1986, and the Video Privacy Protection Act of 1988, among others like them, sought to protect people from the computer equivalent of wiretaps, making it illegal to “listen in” on regular electronic communications.
-
-
She thought a dark moment in her past was forgotten. Then she scanned her face online.
fizkes // Shutterstock
The Health Insurance Portability and Accountability Act is better known by its abbreviation, HIPAA. This influential and wide-reaching law prevents patient information from being shared without patient permission.
In it, HIPAA states that only patients and their authorized representatives are able to access the patient’s health records or information. The act has been in effect for most of the era of mainstream internet use. A key application of HIPAA came up during the coronavirus pandemic in regard to health care providers being required to use secure channels to message or videochat with patients.
fizkes // Shutterstock
The Health Insurance Portability and Accountability Act is better known by its abbreviation, HIPAA. This influential and wide-reaching law prevents patient information from being shared without patient permission.
In it, HIPAA states that only patients and their authorized representatives are able to access the patient’s health records or information. The act has been in effect for most of the era of mainstream internet use. A key application of HIPAA came up during the coronavirus pandemic in regard to health care providers being required to use secure channels to message or videochat with patients.
-
She thought a dark moment in her past was forgotten. Then she scanned her face online.
fizkes // Shutterstock
Keen-eyed observers noticed a Twitter crackdown several years ago when a variety of accounts disappeared because of their listed birthdays. These accounts fell afoul of the Children’s Online Privacy Protection Act, which makes it very legally complex for companies like Twitter to allow users under the age of 13. Of course, on Twitter, this also affected silly pet accounts and organization accounts that listed their founding dates.
It’s not actually illegal for users under 13 to sign up for accounts on these sites. The law outlines exactly how sites could communicate with parents or guardians in order to obtain the right consent. But to do so on a wide scale seems to have intimidated most social networks, for example, which opted to simply ban users under age 13 altogether.
fizkes // Shutterstock
Keen-eyed observers noticed a Twitter crackdown several years ago when a variety of accounts disappeared because of their listed birthdays. These accounts fell afoul of the Children’s Online Privacy Protection Act, which makes it very legally complex for companies like Twitter to allow users under the age of 13. Of course, on Twitter, this also affected silly pet accounts and organization accounts that listed their founding dates.
It’s not actually illegal for users under 13 to sign up for accounts on these sites. The law outlines exactly how sites could communicate with parents or guardians in order to obtain the right consent. But to do so on a wide scale seems to have intimidated most social networks, for example, which opted to simply ban users under age 13 altogether.
-
-
She thought a dark moment in her past was forgotten. Then she scanned her face online.
Mila Supinskaya Glashchenko // Shutterstock
The Gramm–Leach–Billey Act (GLB) accounted for a specific way banks wanted to be able to consolidate different functions, inspired by a real-life merger between a bank and an insurance company. Whether that is or isn’t a good idea is in the eye of the beholder, but the act also goes into detail about some aspects of banking privacy. If you receive an annual privacy notice from your bank, from PayPal, or from any other financial institution, that’s because of the GLB. Banks must disclose how they gather information as well as how that information is to be used. They must also detail how they protect the information.
Mila Supinskaya Glashchenko // Shutterstock
The Gramm–Leach–Billey Act (GLB) accounted for a specific way banks wanted to be able to consolidate different functions, inspired by a real-life merger between a bank and an insurance company. Whether that is or isn’t a good idea is in the eye of the beholder, but the act also goes into detail about some aspects of banking privacy. If you receive an annual privacy notice from your bank, from PayPal, or from any other financial institution, that’s because of the GLB. Banks must disclose how they gather information as well as how that information is to be used. They must also detail how they protect the information.
-
She thought a dark moment in her past was forgotten. Then she scanned her face online.
davidsmith520 // Shutterstock
Hot on the tails of the expiring USA Patriot Act, the USA Freedom Act introduced certain protections for Americans while holding up or introducing new invasions of privacy by the government. The law is also a response to the Edward Snowden leaks describing extensive government monitoring of communications.
The USA Freedom Act is: “An Act to reform the authorities of the Federal Government to require the production of certain business records, conduct electronic surveillance, use pen registers and trap and trace devices, and use other forms of information gathering for foreign intelligence, counterterrorism, and criminal purposes, and for other purposes.”
The law gently juggles what the government is allowed to demand, striking a balance between the post-9/11 Patriot Act and the post-Snowden interest in restoring privacy.
This story originally appeared on Zapproved and was produced and distributed in partnership with Stacker Studio.
davidsmith520 // Shutterstock
Hot on the tails of the expiring USA Patriot Act, the USA Freedom Act introduced certain protections for Americans while holding up or introducing new invasions of privacy by the government. The law is also a response to the Edward Snowden leaks describing extensive government monitoring of communications.
The USA Freedom Act is: “An Act to reform the authorities of the Federal Government to require the production of certain business records, conduct electronic surveillance, use pen registers and trap and trace devices, and use other forms of information gathering for foreign intelligence, counterterrorism, and criminal purposes, and for other purposes.”
The law gently juggles what the government is allowed to demand, striking a balance between the post-9/11 Patriot Act and the post-Snowden interest in restoring privacy.
This story originally appeared on Zapproved and was produced and distributed in partnership with Stacker Studio.


